Security fleets responsible for transporting cash, confidential documents, valuable cargo, or high-profile individuals operate under strict protocols. Every trip is sensitive, every movement matters, and even a minor delay or deviation can raise serious concerns. Whether it is a cash van heading to multiple ATMs or a convoy protecting a VIP, these vehicles must be tracked, controlled, and protected at all times. They must know who is driving, whether the vehicle is following the planned route, what is happening around it, and how quickly they can respond to a crisis. Advanced fleet management software makes this possible. It brings together real-time visibility, accountability, and emergency response tools to protect both people and assets on the move.
Securing security fleet operations with fleet management software
Introduction
Challenges
- No real-time visibility during high-risk movements: Once a security vehicle leaves the control point, managers often have limited or no visibility until it reaches its destination. This gap in monitoring creates uncertainty. If the vehicle stops without explanation, goes off route, or delays its arrival, the central team has no way to act quickly or investigate the reason in real time. For fleets carrying high-value cargo or sensitive individuals, this creates immediate operational and security risks.
- No visual insight into incidents or ongoing trips: Vehicles that operate in high-risk zones may encounter suspicious activity or emergency situations. It becomes difficult for supervisors to understand what is happening. They cannot verify alerts or check whether guards and drivers are following procedures. This lack of evidence also limits post-incident review, making it hard to provide proof or learn from past events.
- Route deviations go unnoticed until it is too late: Security vehicles are often assigned to fixed, pre-approved routes for safety and control. Any off-route driving or wrong turn may go completely unnoticed. By the time someone detects the deviation, the vehicle may already be in an unsafe area or away from its scheduled path. This increases exposure to theft, hijacking, or reputational damage.
- No accountability for who is driving the vehicle: During shift changes or in convoy operations, multiple guards and drivers may use the same vehicle. There is no way to confirm who was operating the vehicle at a specific time. If something goes wrong, from harsh driving to security violations, the lack of individual accountability makes investigation difficult and follow-up actions unclear.
- Risky driving behavior increases the chances of accidents: Security fleet vehicles often operate under pressure, especially when transporting sensitive cargo or following strict timelines. Drivers may unintentionally speed, take sharp turns, or brake harshly during trips. These actions not only endanger the asset and personnel but also increase maintenance needs and insurance risks.
Solution
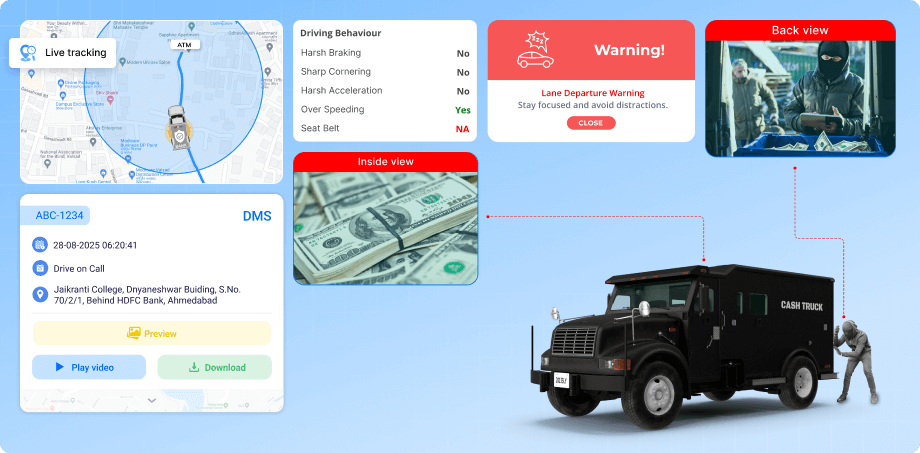
- Live tracking with real-time route monitoring: The software provides continuous live tracking of every vehicle in motion. It automatically detects unusual behavior such as sudden stops, route deviations, or delays and highlights these events on the dashboard. Route history and trip replays are available instantly, offering full visibility of the journey from start to finish without manual input.
- Video telematics for real-time visuals and historical playback: Integrated dashcams stream live video from inside and around the vehicle, while also storing footage for later review. The system allows authorized users to view the vehicle footage, capture critical events, and access video logs linked to specific timestamps or alerts. This supports faster verification during high-risk trips and simplifies incident analysis.
- Geofencing and automated route enforcement: The software enables users to draw precise geofences and define approved travel routes with multiple checkpoints. If a vehicle exits its assigned area or misses a checkpoint, the system flags the event and triggers notifications instantly. Each route deviation is recorded and visualized, reducing manual supervision and improving route discipline across the fleet.
- Driver identification and access logging: Before starting a shift, each driver must authenticate through a unique login or key. This feature links every trip, event, and behavior metric to an individual profile. The system keeps a full audit trail of who operated which vehicle, when, and for how long. Driver-level performance data can also be generated to support safety evaluations and compliance reviews.
- Driving behavior monitoring with automated risk detection: The software automatically tracks key driving parameters, including harsh braking, sudden acceleration, over-speeding, and sharp cornering. Each trip is scored based on safe driving habits and linked to individual driver profiles. This helps identify risky patterns, improve training, and maintain high safety standards during sensitive transport operations. The system generates alerts and reports without the need for manual observation.
Results
- 40% reduction in route deviation cases: Automated geofence alerts and strict route assignment helped vehicles stay on approved paths. This reduced security risks and ensured adherence to operational protocols.
- Fewer delays and improved ETA reliability: Live location tracking and optimized route planning led to better timing accuracy. Sensitive deliveries arrived on schedule with fewer unscheduled stops or detours.
- Better compliance with internal and client protocols: With full visibility into trips, checkpoints, and driver actions, security providers were able to meet contractual standards and audit requirements more consistently.